Subscribe to our blog.
Subscribe NowAPIs are built expressly to share a company's most valuable data and services. That makes them a lucrative target for bad actors. We've already hit the tipping point – APIs are now THE way in.

By 2022, API abuses will move from an infrequent to the most-frequent attack vector, resulting in data breaches for enterprise web applications.
20 November 2017
“Predicts 2018: Infrastructure Protection”
- Strategic Planning Assumption


As 2022 approaches, this prediction could arguably be counted as “missed” – but only because we underestimated the steep rise in attacks on APIs.
06 December 2021
“Predicts 2022: APIs Demand Improved
Security and Management"
Bad actors now target business logic vulnerabilities in your APIs. But since your APIs are unique, it takes them days, weeks, or even months to probe and learn your APIs. They use “low and slow” techniques that WAFs, gateways, and other traditional tools can't detect, leaving you vulnerable.
Past:
One and done
Single step, targeting known vulns (SQLi, XSS), over seconds to minutes
Formulaic attacks, preset


Today:
Low and slow
Multiple steps (look legit), targeting business logic gaps, over days to weeks
Custom attacks, based on recon


Legacy and adjacent tools are trying to pivot
To remain relevant, get into a hot space, or grow their reach, vendors of all stripes are claiming they do API security. You've got the tough job of sorting through all the noise – you need to get clear on what API security really is and the architecture needed to do it right.


Gateways weren’t built for security
IT teams leverage API gateways to publish and update APIs, monitor their usage, facilitate reuse, and enforce schema consistency. But gateways have no ability to monitor API traffic and cannot see the indicators of API manipulation in runtime. That’s why all the gateway vendors partner with Salt for runtime protection.


WAFs can’t see business logic attacks
WAFs, using technology developed 20 years ago, apply rules to protect web apps from yesterday’s attacks, like SQL injections and cross-site scripting. WAFs allow or deny per transaction – they have no ability to stitch together activity over time, so they can’t see today’s API attacks. That’s why, despite the prevalence of WAFs, we see headlines every month of a new company suffering an API breach.

API attacks don’t follow patterns
Every API vulnerability is a zero-day vulnerability, because every company’s APIs are unique and so are their security gaps. Bad actors have to poke and prod to learn your APIs and find mistakes in business logic they can exploit. The only way to catch these attacks is with context – deep behavioral analysis over time. That’s why API security is a whole new category of product needed in your arsenal.

Video: Real-world API Attacks: What your WAF is missing
This comparison shows what API attacks a WAF can spot vs. Salt. We use Postman to launch a combination of more traditional (SQLi, XSS) attacks vs. more sophisticated API attacks. The WAF only has pre-set rules to follow – that’s why it allows the API attack traffic through, whereas Salt spots and blocks the attacks.

Tools like WAFs and API gateways don't have any context for what's happening across APIs and, in turn, cannot effectively detect or protect against exploitation. Salt pulls together all the activity of all users, so it can find and stop attackers in their tracks.
Curtis Simpson, CISO

What sets Salt apart is the ability to analyze your API traffic over days, weeks, and even months, applying cloud scale and mature algorithms to deeply understand your API traffic.
We see more than anyone else, so we stop more attacks than anyone else.
You get:
Better discovery – with smart aggregation of APIs vs. a long list of duplicated endpoints
Better threat protection – with insights spanning months of API usage patterns to spot and stop more attack attempts
Better API hardening – with detailed remediation guidelines based on attackers' minor successful exploits
Salt – Securing your innovation
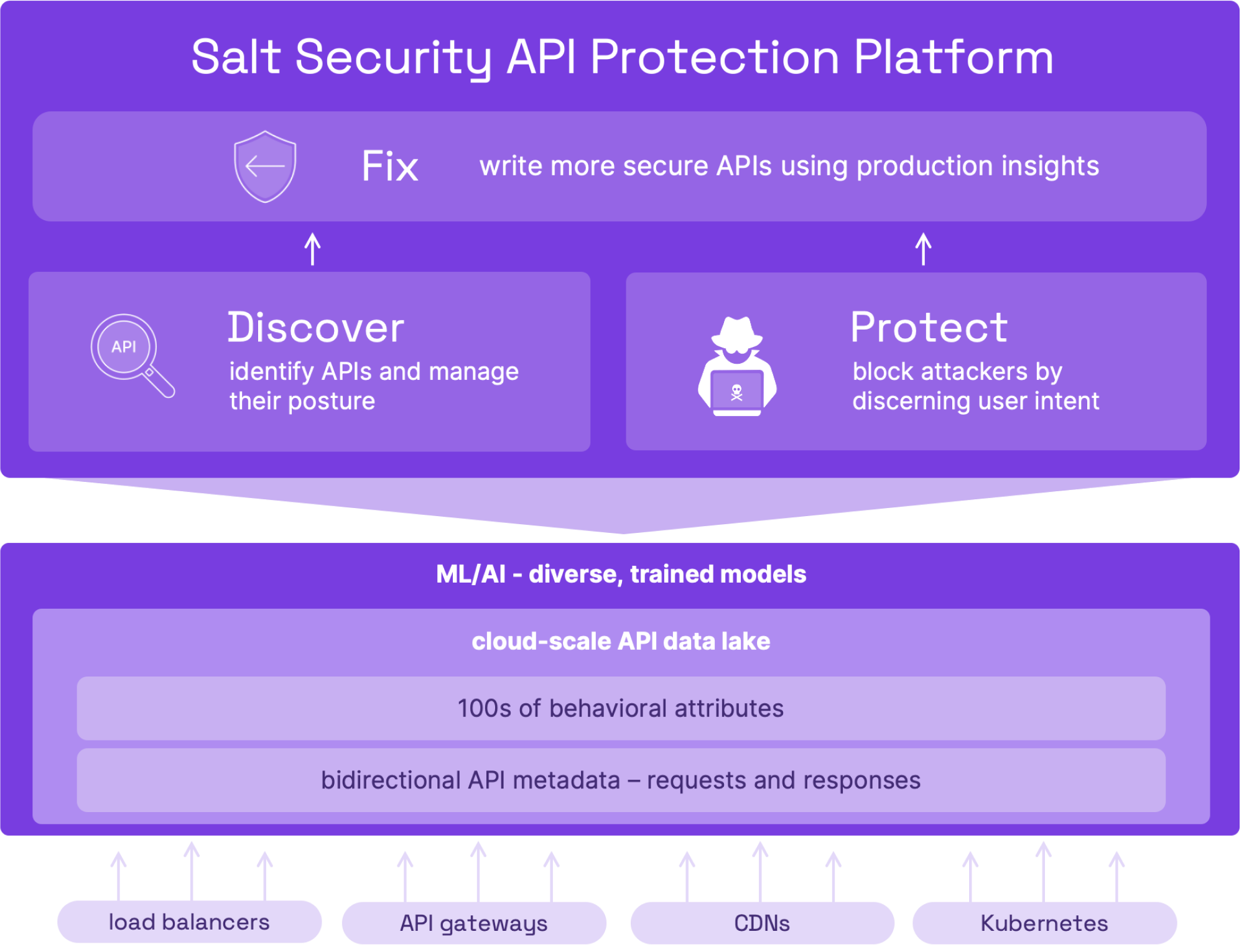
Understanding that attacks themselves are different when APIs are the target is an important starting point for learning how to defend against them. The game has changed – these attacks are rooted in finding business logic flaws, and most solutions aren't up to the task.


We have updated and re-designed our Privacy Policy as of March 2024 to make it easier to understand how we collect and use your personal data.
Read the new policy